Testing KFSensor Windows networking emulation
There are many tools that have been developed to probe and exploit Windows networking. Tools like these may well be used against your KFSensor honeypot system, by hackers.
Note: Many scanners make use of Window's operating system routines to perform a scan. These will not work from the honeypot machine. Always test KFSensor from another machine on your network.
Testing with Windows native commands
Windows includes a very powerful set of commands, which are available from a command console.
These "net" commands provide a simple and powerful way of testing KFSensor without the need to use third party scanners.
To run these tests simply open a DOSBOX on another machine and use the IP address of the KFSensor machine in the examples below.
|
C:\>net time \\192.168.2.9 Current time at \\192.168.2.9 is 10/21/2015 12:01 PM |
The net time command displays the time on the remote computer. This is a simple way of seeing if you have a working connection with a remote computer and a hacker's favorite.
|
C:\>net use * \\192.168.2.9\DOCS Drive Z: is now connected to \\192.168.2.9\DOCS. |
The net use command maps a remote file share to a virtual drive.
|
C:\>net use \\192.168.2.9\ipc$ "" /user:"" The command completed successfully. |
This command opens a null connection on the remote computer.
This indicates a hack is possible.
|
C:\>net view \\192.168.2.9 System error 58 has occurred. The specified server cannot perform the requested operation. |
The net view is used to interrogate a remote domain server. This is not been added to the emulation.
Testing the NBT Name Service
In order to start an NBT Session on port 139 an attacker needs to know the target system's NetBIOS name to establish a session.
So the first stage of an attack is to send a wild card name query to the NBT Name Service.
Note: Attacks launched against SMB direct on port 445 do not need to go through this stage.
These requests usually have the following format:
|
NBT NS Packet: id:256 Op: Name Query Question: *<00 Workstation Service>, Node Status, Internet class |
KFSensor does not attempt to register itself with other Windows machines on the LAN, so it will not appear on My Network Places in Windows explorer.
It will respond to requests sent directly to its IP address.
There are many NetBIOS scanners available.
nbtscan
A reliable and simple command line scanner is nbtscan available from http://www.inetcat.org/software/nbtscan.html.
nbtscan vs. KFSensor
Note: The adapter address is generated by KFSensor at random.|
Doing NBT name scan for adresses from 192.168.2.9 NetBIOS Name Table for Host 192.168.2.9: Incomplete packet, 227 bytes long. Name Service Type ---------------------------------------- GIMLI <00> UNIQUE MORIA <00> GROUP GIMLI <03> UNIQUE GIMLI <20> UNIQUE MORIA <1e> GROUP GIMLID <03> UNIQUE ??__MSBROWSE__? <01> GROUP Adapter address: e8-92-96-33-52-3d ---------------------------------------- |
Testing with a vulnerability scanner
GFI LANguard
GFI LANguard is a popular commercial network security scanner available from http://www.gfi.com/lannetscan/GFI LANguard vs. KFSensor
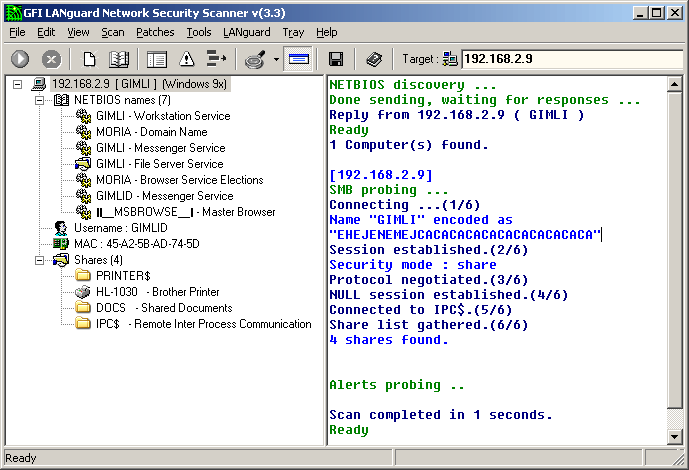
Testing in the wild
One of the most common worms on the Internet is Opaserv.
The worm scans the Internet for Windows 98 machines that do not password protect the administration share.
On establishing a connection with port 139 the worm first writes a copy of its executable to the C:\Windows directory.
It then reads the system file WIN.INI, adds the following line to this file in order to run the worm and then over writes the original.
run=c:\windows\Brasil.exe
Opaserv vs. KFSensor
The following is the KFSensor received event for an W32/Opaserv.worm.d attack.
This will generate the following two files in the upload directory.
200_141_93_72_21145_scrsvr_exe.bin - Worm executable
200_141_93_72_21145_win_ini.bin - Modified system file
|
NBT:1 Session Request Called Name : GIMLI<20 File Server Service> Calling Name: LOCALHOST<20 File Server Service> NBT:2 SMB: [tree con X] {!\\GIMLI\C[00]A:[00]} NBT:3 SMB: [create file] {[04]WINDOWS\scrsvr.exe[00]} NBT:4 SMB: [write] Write 512 bytes at offset 0 .... NBT:60 SMB: [write] Write 259 bytes at offset 28672 NBT:61 SMB: [close file] NBT:62 SMB: [open file] {[04]WINDOWS\win.ini[00]} NBT:63 SMB: [read] Read 512 bytes at offset 0 ... NBT:65 SMB: [read] Read 512 bytes at offset 1024 NBT:66 SMB: [close file] NBT:67 SMB: [create file] {[04]WINDOWS\win.ini[00]} NBT:68 SMB: [write] Write 512 bytes at offset 0 ... NBT:70 SMB: [write] Write 103 bytes at offset 1024 NBT:71 SMB: [close file] |
Related Topics
- Window networking / NetBIOS / SMB / CIFS
- KFSensor Windows networking emulation
- Configuring Windows networking for KFSensor
- NBT Settings
- NetBIOS Name
- Edit Sim Std Server - NBT Name Service
- Edit Sim Std Server - NBT Datagram Service
- Edit Sim Std Server - NBT Session Service
- Edit Sim Std Server - NBT SMB